Arch: signature is unknown trust
Aron Schüler Published
When running your pacman -Syu, you might run into an error about an unknown
trust signature. This is caused by package maintainers changing, dependencies
changing or new ones added. This error does not always mean that someone took
over the package and submitted an insecure package. In this post, I am going to
describe how to fix the error: signature from is unknown trust error.
Why does a package have a signature of unknown trust?
The error you’re seeing is directly related to the pacman-key gpg database. This database contains all necessary PGP public keys. Now, you might ask yourself, whose public keys are necessary? Well, there are two groups who maintain the packages in the official arch repositories. These groups are the official developers and Trusted Users (TU). Packages under their maintenance are always signed by the master keys of these users.
But users in these groups change. For instance, a new user is accepted into the Trusted Users group. That user’s public key must now be added to the archlinux-keyring package. It also must be marked as trusted in the pacman-key gpg database. But this does not happen automatically. Therefore, when that user signs a package, you get the error that the signature is of unknown trust, since the key has not been added to / trusted in the database yet.
How can I trust the signature?
There are at least four options available, with another one being to wait for an
update of archlinux-keyring package. If you want to take matters into your own
hands, I suggest the first option.
First option: Refreshing your trusted keys with pacman-key
Pacman includes a helpful wrapper script for GnuPG. This script is called
pacman-key. You can easily manage your keyring of trusted PGP keys with it.
You can also refresh your local key database with it.
To do so, run the following as root:
pacman-key --refresh-keysOnce this is done, you can check if your desired key is now included. Run this as root:
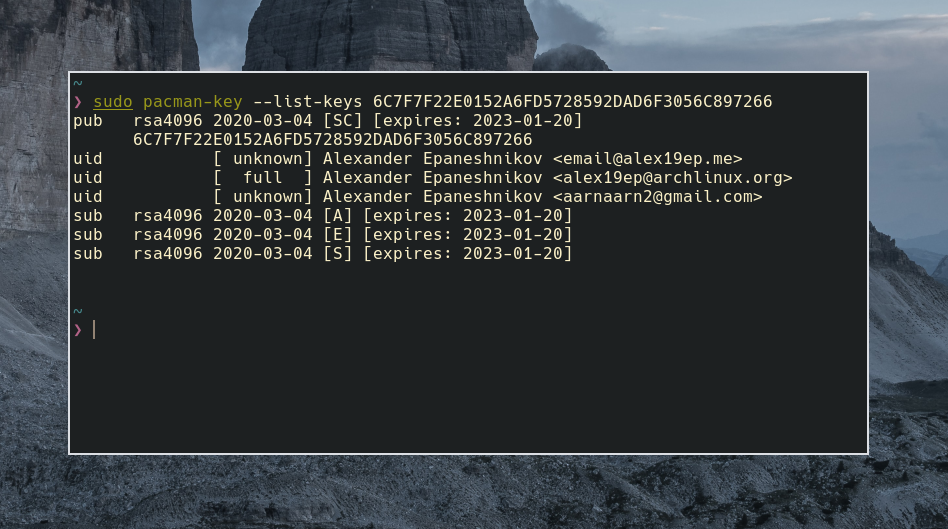
pacman-key --list-keys <signature>For me, I was missing the pub key of Alexander Epaneshnikov, so I will check for his signature:
pacman-key --list-keys 6C7F7F22E0152A6FD5728592DAD6F3056C897266
pub rsa4096 2020-03-04 [SC] [expires: 2023-01-20]
6C7F7F22E0152A6FD5728592DAD6F3056C897266
uid [ unknown] Alexander Epaneshnikov [email protected]e>
uid [ full ] Alexander Epaneshnikov
uid [ unknown] Alexander Epaneshnikov
sub rsa4096 2020-03-04 [A] [expires: 2023-01-20]
sub rsa4096 2020-03-04 [E] [expires: 2023-01-20]
sub rsa4096 2020-03-04 [S] [expires: 2023-01-20]Second option: Reinstalling archlinux-keyring
If you don’t want the hassle of messing with the wrapper script, you can also reinstall the archlinux-keyring package. The post-installation script will update the local pacman gpg database. This can be done by running the following as root:
pacman -S archlinux-keyringAs a result, your key database will be updated and the new key should be included and trusted!
Third option: When everything else fails, do it yourself!
You can also import the key into your pacman keyring yourself. This is necessary when the official keyserver does not provide the desired key (yet). To do so, follow the next steps.
- Import the key into your accounts keyring with
pacman-key --recv-keys <signature>. If you don’t know the signature, googling the<author> pgpshould be enough to give you a result. - Verify the fingerprint to prevent importing bad keys:
pacman-key --finger <signature> - Sign the key locally with your private key, so that the imported key becomes
trusted:
pacman-key --lsign-key <signature>
The key is now included in your pacman database of trusted keys.
Done!
To check if the signature is now contained in your pacman keyring, run
pacman-key --list-keys <signature>. This should result in something like
this:
You successfully imported and trusted the key, nice! Now you can go ahead and update your packages. As a final note, you will notice that this problem occurs more often if you tend to have long periods of time between your upgrades. If this is the case for you, just remember to update your keyring before updating your system, thereby running your upgrade always with a fresh set of public keys. This prevents the signature is unknown trust error on your Arch system while upgrading.
I hope this helped, if it did I’m always happy about a new comment 🙂 If you want to look through my other posts on arch, you can find them here.